How to Monitor PCI DSS Compliance in Real Time
Monitor PCI DSS compliance in real time: map your CDE, deploy SIEM and monitoring tools, automate alerts, and maintain continuous protection against breaches.

If your business handles credit card payments, staying compliant with PCI DSS is mandatory. Real-time monitoring ensures you detect and address risks as they happen, rather than relying on periodic audits that may leave gaps in your security. Here's why it matters:
- Fines for non-compliance: Range from $5,000 to $500,000 per month.
- Data breach costs: Average global breach cost hit $4.88 million in 2024.
- New standards: PCI DSS 4.0 introduces 51 new requirements, fully enforceable by March 2025.
Traditional audits only offer a snapshot of security, leaving vulnerabilities exposed between checks. Real-time monitoring, however, continuously tracks access, alerts for suspicious activity, and ensures compliance with PCI DSS requirements like encryption, change detection, and tamper-proof logs. This approach not only protects sensitive cardholder data but also reduces fraud risks by up to 95%.
Key steps for setting up real-time monitoring include mapping your Cardholder Data Environment (CDE), deploying monitoring tools, and automating alerts. By combining technology with regular audits and employee training, businesses can maintain robust security and compliance every day.
The role of SIEM in PCI DSS compliance
Core Capabilities of Real-Time PCI DSS Monitoring
Real-time monitoring systems play a crucial role in keeping your e-commerce business compliant with PCI DSS. These systems are designed to safeguard cardholder data by integrating key features that provide robust security oversight.
Tracking Access to Cardholder Data
Every time someone accesses your Cardholder Data Environment (CDE), it’s essential to document the event and tie it to a specific user. Avoid using generic accounts, as they make tracking access nearly impossible. Administrative access, particularly the use of "root" or superuser accounts, should be closely monitored. If such accounts are used during off-hours, it should immediately trigger an alert. To comply with PCI DSS Requirement 10, maintain audit trails with logs stored for at least one year, ensuring the most recent three months are readily accessible for review.
Beyond just logging access, automated systems that detect unusual events can significantly strengthen your compliance efforts.
Automated Security Event Alerts
Relying on manual log reviews is too slow to meet real-time compliance needs. A reliable monitoring system should automatically identify suspicious activity, such as brute-force attacks, repeated login failures (with accounts locked after 10 unsuccessful attempts), unauthorized wireless devices, and expired or inactive user accounts. Alerts should be sent instantly via SMS or email when these patterns are detected. Additionally, it’s critical to flag vendor-supplied default accounts and ensure multi-factor authentication (MFA) is enforced for all access to the CDE. Any attempt at non-console administrative or remote access without MFA should also trigger an immediate alert. Advanced systems can go a step further by analyzing real-time account behavior, considering factors like device health, geographic location, and access times to identify potential risks.
Change Detection and Activity Logging
Monitoring critical changes is another essential capability. This includes tracking updates to firewall configurations, security policies, and audit settings. File integrity monitoring tools should be in place to log changes to user IDs, encryption keys, and any unauthorized modifications to payment page scripts. The system must also confirm that anti-malware software is active, up-to-date, and logging detected threats. It should flag any unauthorized or suspicious processes that could signal a breach. Furthermore, ensure cardholder data is encrypted both at rest and in transit using strong cryptographic protocols like TLS 1.2 or higher. If unencrypted traffic or weak encryption methods are detected, the system should immediately alert you. These features provide the real-time insights needed to maintain compliance and quickly respond to potential threats.
How to Set Up Real-Time PCI DSS Monitoring
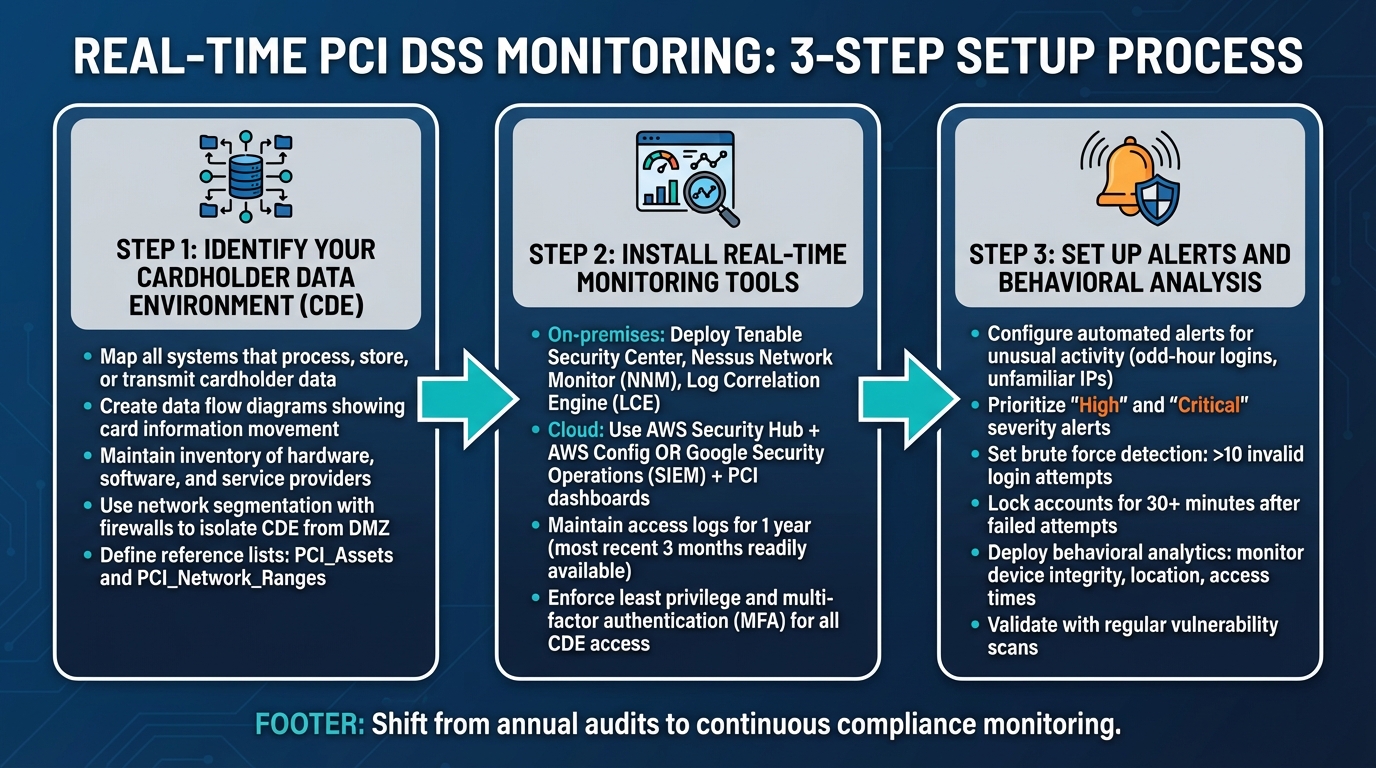
3-Step Process to Set Up Real-Time PCI DSS Monitoring
Creating a real-time monitoring system for PCI DSS compliance starts with understanding your environment and ends with implementing smart automation. The process begins by mapping all systems that interact with payment data, ensuring a strong foundation for real-time protection.
Step 1: Identify Your Cardholder Data Environment (CDE)
The first step is to clearly define your Cardholder Data Environment (CDE). This means identifying all systems that process, store, or transmit cardholder data, such as web servers, payment gateways, databases, and third-party services involved in transactions.
"Identify every system, application, and network that touches cardholder data. Create a data flow diagram that shows exactly how card information moves through your environment, from the point of entry (e.g., website, terminal, app) to where it's processed or stored." - Stripe
To make this process thorough, map out the flow of cardholder data through a detailed diagram. This should include every point of interaction, from the initial entry to final storage. Keep an up-to-date inventory of all hardware, software, and service providers involved in the payment process.
Network segmentation is key. Use firewalls to isolate the CDE from other parts of your network, such as the demilitarized zone (DMZ). This prevents attackers from moving laterally if they breach your defenses and reduces the scope of systems subject to PCI DSS requirements.
Additionally, define reference lists for your monitoring tools, such as PCI_Assets and PCI_Network_Ranges, to ensure dashboards focus only on relevant systems. If a system doesn’t need to handle cardholder data, exclude it from the CDE to simplify compliance.
Once the CDE is clearly mapped, you can move on to setting up monitoring tools.
Step 2: Install Real-Time Monitoring Tools
After mapping the CDE, deploy monitoring platforms to track system activity and spot vulnerabilities in real time. For on-premises setups, tools like Tenable Security Center provide continuous network monitoring with deep packet inspection. Tenable Nessus Network Monitor (NNM) focuses on database tracking, while Tenable Log Correlation Engine (LCE) monitors vulnerabilities across your infrastructure.
If you’re working with cloud-based platforms, AWS Security Hub is a great option for identifying vulnerabilities in resources handling cardholder data. Combine this with AWS Config for continuous resource monitoring. On Google Cloud, use Google Security Operations (SIEM) and PCI dashboards to monitor access, identity, and network activity.
Access logging is critical. Maintain detailed logs for at least one year, with the most recent three months readily available. Enforce least privilege and multi-factor authentication (MFA) for all access, especially non-console administrative and remote access to the CDE, as required by PCI DSS v4.0.
Once these tools are in place, focus on setting up proactive alerts.
Step 3: Set Up Alerts and Behavioral Analysis
This step shifts your monitoring tools from passive observation to active defense. Set up automated alerts to flag unusual activity, such as administrative logins at odd hours or from unfamiliar IP addresses. Prioritize "High" and "Critical" severity alerts to manage threats effectively and prevent alert fatigue.
For example, configure alerts for brute force attacks by monitoring for more than 10 invalid login attempts within a short period. Accounts locked due to failed logins should remain locked for at least 30 minutes or until identity verification is completed. Correlation searches can also detect unauthorized changes, such as firewall modifications or unexpected network device reboots.
"Dynamically analyzing an account's security posture... allows for more rapid detection and response to address potentially compromised credentials." - Splunk PCI Compliance Documentation
Behavioral analytics can further enhance security by monitoring device integrity, location, access times, and resource usage in real time. Set rules to detect sensitive data transmissions and deploy endpoint detection and response (EDR) sensors to prioritize active threats.
Finally, validate alerts and system changes through regular vulnerability scans. This ensures your monitoring system remains effective and aligned with PCI DSS requirements. By combining proactive alerts with continuous monitoring, you can maintain a strong defense against security risks.
Maintaining Continuous PCI DSS Compliance
Getting started with PCI DSS compliance often begins with real-time monitoring, but keeping it up requires consistent, daily security practices. This means shifting from the mindset of annual audits to embedding security measures into everyday operations. Compliance should be a continuous process, not a yearly checkbox.
"This guidance aims to help organizations understand how to incorporate continuous security and compliance practices into their culture and daily operational activities." - Emma Sutcliffe, Senior Director of Data Security Standards, PCI SSC
Schedule Regular Compliance Audits
After setting up real-time alerts, maintaining compliance demands ongoing reviews to ensure all activities align with PCI DSS standards.
The frequency and type of audits depend on the volume of transactions your business handles. Level 1 merchants (processing 6 million or more transactions annually) are required to complete an annual Report on Compliance (ROC), which must be conducted by a Qualified Security Assessor (QSA). Levels 2-4 merchants, handling fewer transactions, generally complete an annual Self-Assessment Questionnaire (SAQ).
To stay compliant, combine these annual reviews with quarterly vulnerability scans and monthly access reviews. Automated tools can simplify evidence gathering, and critical vendor security patches should be installed within 30 days of release.
Connect Compliance Monitoring with Business Systems
Centralizing your compliance metrics is key to simplifying oversight. By integrating monitoring tools with platforms like a SIEM (Security Information and Event Management) system, you can align detection rules with PCI DSS 4.0 standards, making real-time compliance checks easier.
You can also automate access reviews by linking compliance tools with your HRIS (Human Resource Information System). This setup flags risky accounts, such as those tied to employees who have left the company or transferred to different roles, reducing potential vulnerabilities.
Train Employees on Security Requirements
Technology plays a big role in compliance, but well-trained employees are just as critical. A strong compliance program blends automated monitoring with informed, security-conscious staff.
People are at the heart of compliance efforts. PCI DSS Requirement 12 emphasizes the importance of security policies and training programs for all employees. To meet this, businesses should roll out targeted training, including phishing simulations, and track participation through automated systems.
Training should focus on common threats like phishing and social engineering, as attackers often exploit human error to access sensitive information. Many training modules are designed to be quick - some taking as little as 30 minutes - so they don’t disrupt daily operations.
Additionally, employees should regularly review and acknowledge security policies through a centralized system to ensure compliance records are up to date. Update training content to include PCI DSS 4.0 requirements, such as script security and e-skimming prevention (Requirements 6.4.3 and 11.6.1), to protect against unauthorized changes to client-side scripts.
Conclusion
Real-time monitoring transforms PCI DSS compliance from a one-time task into an ongoing effort to ensure security. For ecommerce businesses, this means detecting threats as they occur - whether it’s unauthorized access attempts, configuration changes, or suspicious activity. This proactive approach allows security teams to address potential issues before they escalate into costly breaches, creating a stronger and more adaptive security strategy.
"The point [of continuous validation] is to catch problems before they become breaches and to show that your controls hold up under scrutiny." - Stripe
The financial risks are hard to ignore. With the average global data breach projected to cost $4.88 million in 2024, investing in effective monitoring tools and processes is essential - not just for compliance but for protecting your business. Automated alerts provide immediate warnings about unusual activity, while continuous vulnerability tracking catches threats that periodic scans might overlook.
However, technology alone isn’t enough. Success depends on combining advanced monitoring with a knowledgeable workforce. While automated systems handle tasks like tracking access logs and monitoring configuration changes, employees play a key role in maintaining security. A team that understands its responsibilities, paired with cutting-edge tools, creates a strong defense against evolving threats.
"Complying with PCI DSS shows customers you're committed to protecting their financial information, which builds trust and loyalty." - Rebecca Rosenberg, Shopify
FAQs
What are the key updates in PCI DSS 4.0?
PCI DSS 4.0 brings in several updates designed to improve payment security and address evolving threats. Some of the key changes include:
- Stronger Security Controls: The standard introduces more robust measures to safeguard sensitive data and reduce vulnerabilities.
- Focus on Continuous Monitoring: Organizations are encouraged to maintain ongoing oversight of their security systems rather than relying solely on periodic assessments.
- Risk-Based Compliance: A flexible approach allows businesses to tailor security measures based on their specific risks and operational needs.
Another noteworthy change is the revision of reporting requirements. These updates aim to simplify documentation, ensuring compliance efforts are clearly and consistently recorded. Together, these enhancements are designed to help businesses protect cardholder data more effectively while staying prepared for emerging security challenges.
How does real-time monitoring help reduce fraud risks significantly?
Real-time monitoring plays a crucial role in cutting down fraud risks by allowing businesses to spot and respond to suspicious activities instantly. Whether it's unauthorized access attempts or unexpected changes in payment systems, this quick action helps close the gap for potential breaches. The result? Sensitive customer data stays protected, and businesses maintain compliance with PCI DSS standards.
By keeping a constant eye on systems and identifying anomalies as they happen, companies can stop fraud in its tracks. This approach has been shown to reduce risks by as much as 95%, providing a strong layer of protection for ecommerce operations.
Why is network segmentation crucial for maintaining PCI DSS compliance?
Network segmentation is key to maintaining PCI DSS compliance because it separates the cardholder data environment (CDE) from the rest of your network. This separation not only helps protect sensitive payment data but also reduces the overall scope of compliance efforts, making the process more manageable.
By restricting access to the CDE, segmentation lowers the chances of unauthorized access and potential data breaches. It also streamlines monitoring and auditing tasks, helping ensure your systems stay secure and aligned with PCI DSS requirements.





